Computer networks miscellaneous
- Assume that source S and destination D are connected through two intermediate routers labelled R. Determine how many times each packet has to visit the network layer and the data link layer during a transmission from S to D.
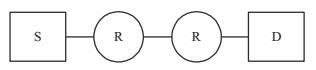
-
View Hint View Answer Discuss in Forum
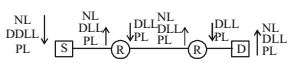
∴ Each packet has to visit the network layer 4 times and the data link layer 6 times during a transmission from S to D. The answer is (c) NL-4 times and DLL-6 timesCorrect Option: C

∴ Each packet has to visit the network layer 4 times and the data link layer 6 times during a transmission from S to D. The answer is (c) NL-4 times and DLL-6 times
- Identify the correct order in which the following actions take place in an interaction between a web browser and a web server.
1. The web browser requests a webpage using HTTP.
2. The web browser establishes a TCP connection with the web server.
3. The web server sends the requested webpage using HTTP.
4. The web browser resolves the domain name using DNS.
-
View Hint View Answer Discuss in Forum
First the web-browser resolves the domain name using DNS (i.e. finding the IP address of the server specified in the URL). Then a TCP connection is established between web browser & the server After that the web browser requests a webpage using HTTP..., Finally the web server sends the requested webpage using HTTP.
Correct Option: A
First the web-browser resolves the domain name using DNS (i.e. finding the IP address of the server specified in the URL). Then a TCP connection is established between web browser & the server After that the web browser requests a webpage using HTTP..., Finally the web server sends the requested webpage using HTTP.
Direction: Frames of 1000 bits are sent over a 106 bps duplex link between two hosts. The propagation time is 25 ms. Frames are to be transmitted into this link to maximally pack them in transit (within the link).
- Suppose that the sliding window protocol is used with the sender window size of 21, where 1 is the number of its identified in the earlier part and acknowledgments are always piggy backed. After sending 21 frames, what is the minimum time, the sender will have to wait before starting transmission of the next frame? (Identify the closest choice ignoring the frame processing time.)
-
View Hint View Answer Discuss in Forum
Time taken to send 10^6 bits = 1 s
Now, as 1 frame = 1000 bits
Time taken to send 2^5 frames = 32 ms
Also, Time taken for first frame to be acknowledged = 25 × 2 = 50 ms
Hence, the waiting time = 50 – 32 = 18 msCorrect Option: B
Time taken to send 10^6 bits = 1 s
Now, as 1 frame = 1000 bits
Time taken to send 2^5 frames = 32 ms
Also, Time taken for first frame to be acknowledged = 25 × 2 = 50 ms
Hence, the waiting time = 50 – 32 = 18 ms
- What is the minimum number of bits l that will be required to represent the sequence numbers distinctly? Assume that no time gap need to be given between transmission of two frames.
-
View Hint View Answer Discuss in Forum
Pulse rate = Number of bits = 1000 = 4 × 104 Time taken 25 × 10-3
Now, Bit rate = Pulse rate × 21
21 = 25 ⇒ I = 5Correct Option: D
Pulse rate = Number of bits = 1000 = 4 × 104 Time taken 25 × 10-3
Now, Bit rate = Pulse rate × 21
21 = 25 ⇒ I = 5
- In serial data transmission, every byte of data is padded with a ‘0’ in the beginning and one or two 1’s at the end of byte because
-
View Hint View Answer Discuss in Forum
The primary use of padding is to prevent the cryptanalyst from using that predictability to find cribs that aid in breaking the encryption. Hence, padding bits are used to protect the bits. All the bytes that are required to be padded are padded with zero.
There are two types of padding methods: Bit padding/Byte padding and Zero padding.
Bit Padding : Two types of bits are used in the process: Single set bit generally represented by 1 and Reset Bit 0. A single set (1) bit is added to a message and then as many reset (0) bits as necessary are added to the same message. The total number of reset (0) bits added actually depends on the boundary of the message to which the message needs to be extended. In bit terms this is 1000... 0000, in hex byte terms this is 80 00... 0000.
For example, a message of 23 bit that is padded with 9 bits in order to fill a 32 bit block ... | 1011 1001 1101 0100 0010 0111 0000 0000|
Zero Padding : In zero padding, all bytes are padded with zero.
Example: In the following example the block size is 8 byte and padding is required for 4 byte ... |DD DD DD DD DD DD DD DD| DD DD DD DD 00 00 00 00 | Zero padding makes it impossible to distinguish between plain text data bytes and padding bytes as it is not reversible in the case when original file ends with one or more zero bytesCorrect Option: A
The primary use of padding is to prevent the cryptanalyst from using that predictability to find cribs that aid in breaking the encryption. Hence, padding bits are used to protect the bits. All the bytes that are required to be padded are padded with zero.
There are two types of padding methods: Bit padding/Byte padding and Zero padding.
Bit Padding : Two types of bits are used in the process: Single set bit generally represented by 1 and Reset Bit 0. A single set (1) bit is added to a message and then as many reset (0) bits as necessary are added to the same message. The total number of reset (0) bits added actually depends on the boundary of the message to which the message needs to be extended. In bit terms this is 1000... 0000, in hex byte terms this is 80 00... 0000.
For example, a message of 23 bit that is padded with 9 bits in order to fill a 32 bit block ... | 1011 1001 1101 0100 0010 0111 0000 0000|
Zero Padding : In zero padding, all bytes are padded with zero.
Example: In the following example the block size is 8 byte and padding is required for 4 byte ... |DD DD DD DD DD DD DD DD| DD DD DD DD 00 00 00 00 | Zero padding makes it impossible to distinguish between plain text data bytes and padding bytes as it is not reversible in the case when original file ends with one or more zero bytes

