Computer networks miscellaneous
- An IP machine Q has a path to another IP machine H via three IP routers R1, R2, and R3.
Q—R1—R2—R3—H
H acts as an HTTP server, and Q connects to H via HTTP and downloads a file. Session layer encryption is used, with DES as the shared key encryption protocol. Consider the following four pieces of information:
[I1] The URL of the file downloaded by Q
[I2] The TCP port numbers at Q and H
[I3] The IP addresses of Q and H
[I4] The link layer addresses of Q and H Which of I1, I2, I3, and I4 can an intruder learn through sniffing at R2 alone?
-
View Hint View Answer Discuss in Forum
Sniffing at R2 alone, an intruder can learn the TCP port numbers and IP address of Q and H.
Correct Option: C
Sniffing at R2 alone, an intruder can learn the TCP port numbers and IP address of Q and H.
- Which one of the following socket API functions converts an unconnected active TCP socket into a passive socket?
-
View Hint View Answer Discuss in Forum
Listen converts active unconnected mode to passive mode, indicating that the kernal should accept incoming connection requests directed to this socket.
Correct Option: C
Listen converts active unconnected mode to passive mode, indicating that the kernal should accept incoming connection requests directed to this socket.
- Consider the following statements
I. TCP connections are full duplex
II. TCP has no option for selective acknowledgment
III. TCP connections are message streams
-
View Hint View Answer Discuss in Forum
I : TCP allows full – duplex communication. This is TRUE statement. TCP is a full-duplex protocol; it allows both parties to send and receive data within the context of the single TCP connection.
II : TCP has no option for selective acknowledgments. This is FALSE statement. TCP may experience poor performance when multiple packets are lost from one window of data. With the limited information available from cumulative acknowledgments, a TCP sender can only learn about a single lost packet per round trip time. An aggressive sender could choose to retransmit packets early, but such retransmitted segments may have already been successfully received. A Selective Acknowledgment (SACK) mechanism, combined with a selective repeat retransmission policy, can help to overcome these limitations. The receiving TCP sends back SACK packets to the sender informing the sender of data that has been received. The sender can then retransmit only the missing data segments.
III : TCP work as a message stream. This is FALSE statement. In TCP, Data is read as a byte stream, no distinguishing indications are transmitted to signal message (segment) boundaries.Correct Option: A
I : TCP allows full – duplex communication. This is TRUE statement. TCP is a full-duplex protocol; it allows both parties to send and receive data within the context of the single TCP connection.
II : TCP has no option for selective acknowledgments. This is FALSE statement. TCP may experience poor performance when multiple packets are lost from one window of data. With the limited information available from cumulative acknowledgments, a TCP sender can only learn about a single lost packet per round trip time. An aggressive sender could choose to retransmit packets early, but such retransmitted segments may have already been successfully received. A Selective Acknowledgment (SACK) mechanism, combined with a selective repeat retransmission policy, can help to overcome these limitations. The receiving TCP sends back SACK packets to the sender informing the sender of data that has been received. The sender can then retransmit only the missing data segments.
III : TCP work as a message stream. This is FALSE statement. In TCP, Data is read as a byte stream, no distinguishing indications are transmitted to signal message (segment) boundaries.
- Host A sends a UDP datagram containing 8880 bytes of user data to host B over an Ethernet LAN. Ethernet frames may carry data up to 1500 bytes (i.e. MTU = 1500 bytes).Size of UDP header is 8 bytes and size of IP header is 20 bytes. There is no option field in IP header. How many total number of IP fragments will be transmitted and what will be the contents of offset field in the last fragment?
-
View Hint View Answer Discuss in Forum
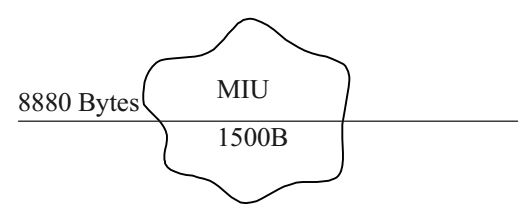
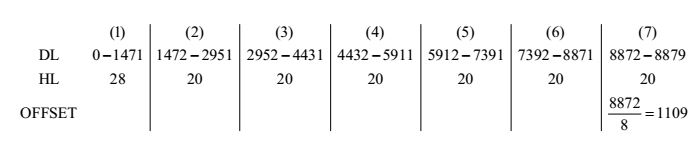
Correct Option: C


- Assume that the bandwidth for a TCP connection is 1048560 bits/sec. Let a be the value of RIT in milliseconds (rounded off to the nearest integer) after which the TCP window scale option is needed. Let b be the maximum possible window size with window scale option. Then the values of a and b are
-
View Hint View Answer Discuss in Forum
NA
Correct Option: C
NA

